This page describes the command line tools for encryption and decryption. Enc is used for various block and stream ciphers using keys based on passwords or explicitly provided. It can also be used for Base64 encoding or decoding.
- Openssl Generate Aes 256 Key Detection
- Openssl Generate Aes 256 Key Size
- Openssl Generate Aes 256 Key
- Openssl Generate Random Aes 256 Key
- Openssl Generate Aes 256 Keys
- Openssl Generate Aes 256 Key Base64
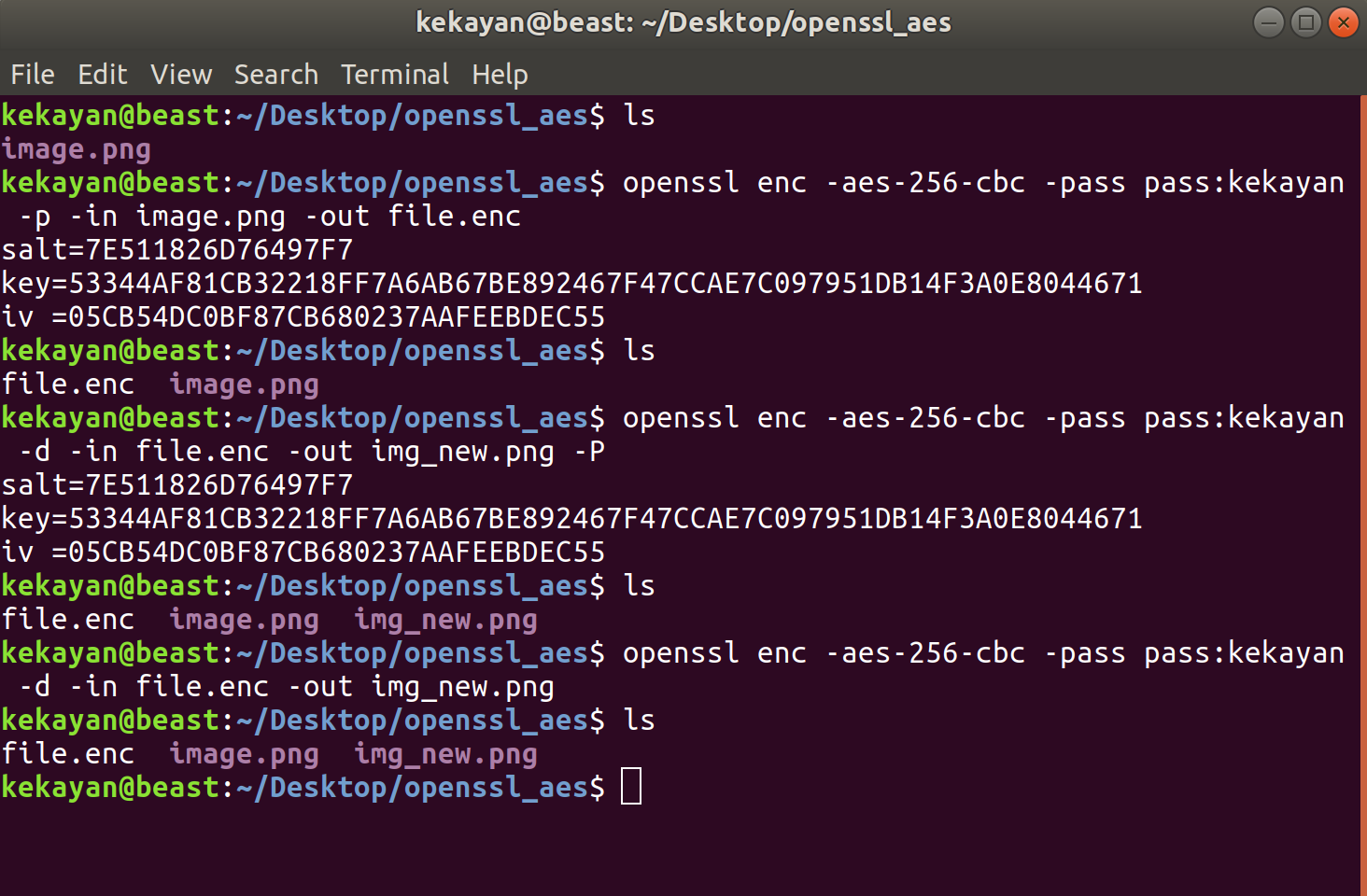
$ openssl enc -aes-256-cbc -e -iter 1000 -salt -in primes.dat -out primes.enc enter aes-256-cbc encryption password: Verifying - enter aes-256-cbc encryption password: The analogous decryption command is as follows: $ openssl enc -aes-256-cbc -d -iter 1000 -in primes.enc -out primes.dec enter aes-256-cbc decryption password: Commands. This might be a noob question, but I couldn't find its answer anywhere online: why does an OpenSSL generated 256-bit AES key have 64 characters? The command I'm using to generate the key. OpenSSL is well known for its ability to generate certificates but it can also be used to generate random data. Generates 32 random bytes (256bits) in a base64 encoded output: openssl rand -base64 32 Plaintext. Generates 32 random characters (256bits): openssl rand 32.
- 4Examples
- 4.2Encryption
Synopsis[edit]
Openssl Generate Aes 256 Key Detection
The basic usage is to specify a ciphername and various options describing the actual task.
You can obtain an incomplete help message by using an invalid option, eg. -help.
Cipher alogorithms[edit]
To get a list of available ciphers you can use the list -cipher-algorithms command
The output gives you a list of ciphers with its variations in key size and mode of operation. For example AES-256-CBC for AES with key size 256 bits in CBC-mode. Some ciphers also have short names, for example the one just mentioned is also known as aes256. These names are case insensitive. In addition none is a valid ciphername. This algorithms does nothing at all.
Options[edit]
The list of options is rather long.
- -in filename
- This specifies the input file.
- -out filename
- This specifies the output file. It will be created or overwritten if it already exists.
- -e or -d
- This specifies whether to encrypt (-e) or to decrypt (-d). Encryption is the default. Of course you have to get all the other options right in order for it to function properly. In particular it is necessary to give the correct cipher-name as well as -a, -A or -z options.
- -a, -A, -base64
- These flags tell OpenSSL to apply Base64-encoding before or after the cryptographic operation. The -a and -base64 are equivalent. If you want to decode a base64 file it is necessary to use the -d option. By default the encoded file has a line break every 64 characters. To suppress this you can use in addition to -base64 the -A flag. This will produce a file with no line breaks at all. You can use these flags just for encoding Base64 without any ciphers involved.
- -bufsize n
- Specify the buffer size. This concerns only internal buffers. It has nothing to do with the cryptographic algorithms in question.
- -debug
- Enable debugging output. This does not include any sensitive information. See also -P.
- -engine id
- Specify an engine for example to use special hardware.
- -iv IV
- This specifies the initialization vectorIV as hexadecimal number. If not explicitly given it will be derived from the password. See key derivation for details.
- -k password, -kfile filename
- Both option are used to specify a password or a file containing the password which is used for key derivation. However they are deprecated. You should use the -pass option instead. The equivalents are -pass pass:password and -pass file:filename respectively.
- -K key
- This option allows you to set the key used for encryption or decryption. This is the key directly used by the cipher algorithm. If no key is given OpenSSL will derive it from a password. This process is described in PKCS5#5 (RFC-2898).
- -md messagedigest
- This specifies the message digest which is used for key derivation. It can take one of the values md2, md5, sha or sha1.
- -nopad
- This disables standard padding.
- -salt, -nosalt, -S salt
- These options allow to switch salting on or off. With -Ssalt it is possible to explicitly give its value (in hexadecimal).
- -p, -P
- Additionally to any encryption tasks, this prints the key, initialization vector and salt value (if used). If -P is used just these values are printed, no encryption will take place.
- -pass arg
- This specifies the password source. Possible values for arg are pass:password or file:filename, where password is your password and filename file containing the password.
- -z
- Use this flag to enable zlib-compression. After a file is encrypted (and maybe base64 encoded) it will be compressed via zlib. Vice versa while decrypting, zlib will be applied first.
Examples[edit]
Base64 Encoding[edit]
To encode a file text.plain you can use
To decode a file the the decrypt option (-d) has to be used
Encryption[edit]
Basic Usage[edit]
The most basic way to encrypt a file is this
It will encrypt the file some.secret using the AES-cipher in CBC-mode. The result will be Base64 encoded and written to some.secret.enc. OpenSSL will ask for password which is used to derive a key as well the initialization vector.Since encryption is the default, it is not necessary to use the -e option.
Use a given Key[edit]
It also possible to specify the key directly. For most modes of operations (i.e. all non-ECB modes) it is then necessary to specify an initialization vector. Usually it is derived together with the key form a password. And as there is no password, also all salting options are obsolete.
The key and the IV are given in hex. Their length depending on the cipher and key size in question.
The key above is one of 16 weak DES keys. It should not be used in practice.
by Alexey Samoshkin
Most common OpenSSL commands and use cases
When it comes to security-related tasks, like generating keys, CSRs, certificates, calculating digests, debugging TLS connections and other tasks related to PKI and HTTPS, you’d most likely end up using the OpenSSL tool.
OpenSSL includes tonnes of features covering a broad range of use cases, and it’s difficult to remember its syntax for all of them and quite easy to get lost. man pages are not so helpful here, so often we just Google “openssl how to [use case here]” or look for some kind of “openssl cheatsheet” to recall the usage of a command and see examples.
This post is my personal collection of openssl command snippets and examples, grouped by use case.
Use cases
Here is a list of use cases, that I’ll be covering:
Surely, this is not a complete list, but it covers the most common use cases and includes those I’ve been working with. For example, I skip encryption and decryption, or using openssl for CA management. openssl is like a universe. You never know where it ends. ?
Working with RSA and ECDSA keys
In the commands below, replace [bits] with the key size (For example, 2048, 4096, 8192).
Generate an RSA key:openssl genrsa -out example.key [bits]
Print public key or modulus only:openssl rsa -in example.key -puboutopenssl rsa -in example.key -noout -modulus
Print textual representation of RSA key:openssl rsa -in example.key -text -noout
Generate new RSA key and encrypt with a pass phrase based on AES CBC 256 encryption:openssl genrsa -aes256 -out example.key [bits]
Check your private key. If the key has a pass phrase, you’ll be prompted for it:openssl rsa -check -in example.key
Remove passphrase from the key:openssl rsa -in example.key -out example.key
Encrypt existing private key with a pass phrase:openssl rsa -des3 -in example.key -out example_with_pass.key
Generate ECDSA key. curve is to be replaced with: prime256v1, secp384r1, secp521r1, or any other supported elliptic curve:openssl ecparam -genkey -name [curve] | openssl ec -out example.ec.key
Print ECDSA key textual representation:openssl ec -in example.ec.key -text -noout
List available EC curves, that OpenSSL library supports:openssl ecparam -list_curves
Generate DH params with a given length:openssl dhparam -out dhparams.pem [bits]
Create certificate signing requests (CSR)
In the commands below, replace [digest] with the name of the supported hash function: md5, sha1, sha224, sha256, sha384 or sha512, etc. It’s better to avoid weak functions like md5 and sha1, and stick to sha256 and above.
Create a CSR from existing private key.openssl req -new -key example.key -out example.csr -[digest]
Create a CSR and a private key without a pass phrase in a single command:openssl req -nodes -newkey rsa:[bits] -keyout example.key -out example.csr
Provide CSR subject info on a command line, rather than through interactive prompt.openssl req -nodes -newkey rsa:[bits] -keyout example.key -out example.csr -subj '/C=UA/ST=Kharkov/L=Kharkov/O=Super Secure Company/OU=IT Department/CN=example.com'
Create a CSR from existing certificate and private key:openssl x509 -x509toreq -in cert.pem -out example.csr -signkey example.key
Generate a CSR for multi-domain SAN certificate by supplying an openssl config file:openssl req -new -key example.key -out example.csr -config req.conf

where req.conf:
Create X.509 certificates
Create self-signed certificate and new private key from scratch:openssl req -nodes -newkey rsa:2048 -keyout example.key -out example.crt -x509 -days 365
Create a self signed certificate using existing CSR and private key:openssl x509 -req -in example.csr -signkey example.key -out example.crt -days 365
Sign child certificate using your own “CA” certificate and it’s private key. If you were a CA company, this shows a very naive example of how you could issue new certificates.openssl x509 -req -in child.csr -days 365 -CA ca.crt -CAkey ca.key -set_serial 01 -out child.crt
Print textual representation of the certificateopenssl x509 -in example.crt -text -noout
Print certificate’s fingerprint as md5, sha1, sha256 digest:openssl x509 -in cert.pem -fingerprint -sha256 -noout
Verify CSRs or certificates
Verify a CSR signature:openssl req -in example.csr -verify
Verify that private key matches a certificate and CSR:openssl rsa -noout -modulus -in example.key | openssl sha256openssl x509 -noout -modulus -in example.crt | openssl sha256openssl req -noout -modulus -in example.csr | openssl sha256
Verify certificate, provided that you have root and any intemediate certificates configured as trusted on your machine:openssl verify example.crt
Verify certificate, when you have intermediate certificate chain. Root certificate is not a part of bundle, and should be configured as a trusted on your machine.openssl verify -untrusted intermediate-ca-chain.pem example.crt
Verify certificate, when you have intermediate certificate chain and root certificate, that is not configured as a trusted one.openssl verify -CAFile root.crt -untrusted intermediate-ca-chain.pem child.crt
Verify that certificate served by a remote server covers given host name. Useful to check your mutlidomain certificate properly covers all the host names.openssl s_client -verify_hostname www.example.com -connect example.com:443
Calculate message digests and base64 encoding
Calculate md5, sha1, sha256, sha384, sha512digests:openssl dgst -[hash_function] <input.filecat input.file | openssl [hash_function]
Base64 encoding and decoding:cat /dev/urandom | head -c 50 | openssl base64 | openssl base64 -d
TLS client to connect to a remote server
Connect to a server supporting TLS:openssl s_client -connect example.com:443openssl s_client -host example.com -port 443
Connect to a server and show full certificate chain:openssl s_client -showcerts -host example.com -port 443 </dev/null
Extract the certificate:openssl s_client -connect example.com:443 2>&1 < /dev/null | sed -n '/-----BEGIN/,/-----END/p' > certificate.pem
Override SNI (Server Name Indication) extension with another server name. Useful for testing when multiple secure sites are hosted on same IP address:openssl s_client -servername www.example.com -host example.com -port 443
Test TLS connection by forcibly using specific cipher suite, e.g. ECDHE-RSA-AES128-GCM-SHA256. Useful to check if a server can properly talk via different configured cipher suites, not one it prefers.openssl s_client -host example.com -port 443 -cipher ECDHE-RSA-AES128-GCM-SHA256 2>&1 </dev/null
Measure TLS connection and handshake time
Measure SSL connection time without/with session reuse:openssl s_time -connect example.com:443 -newopenssl s_time -connect example.com:443 -reuse
Roughly examine TCP and SSL handshake times using curl:curl -kso /dev/null -w 'tcp:%{time_connect}, ssldone:%{time_appconnect}n' https://example.com
Measure speed of various security algorithms:openssl speed rsa2048openssl speed ecdsap256
Convert between encoding and container formats
Convert certificate between DER and PEM formats:openssl x509 -in example.pem -outform der -out example.deropenssl x509 -in example.der -inform der -out example.pem
Combine several certificates in PKCS7 (P7B) file:openssl crl2pkcs7 -nocrl -certfile child.crt -certfile ca.crt -out example.p7b
Convert from PKCS7 back to PEM. If PKCS7 file has multiple certificates, the PEM file will contain all of the items in it.openssl pkcs7 -in example.p7b -print_certs -out example.crt
Combine a PEM certificate file and a private key to PKCS#12 (.pfx .p12). Also, you can add a chain of certificates to PKCS12 file.openssl pkcs12 -export -out certificate.pfx -inkey privkey.pem -in certificate.pem -certfile ca-chain.pem
Convert a PKCS#12 file (.pfx .p12) containing a private key and certificates back to PEM:openssl pkcs12 -in keystore.pfx -out keystore.pem -nodes
List cipher suites
List available TLS cipher suites, openssl client is capable of:openssl ciphers -v
Enumerate all individual cipher suites, which are described by a short-hand OpenSSL cipher list string. This is useful when you’re configuring server (like Nginx), and you need to test your ssl_ciphers string.openssl ciphers -v 'EECDH+ECDSA+AESGCM:EECDH+aRSA+SHA256:EECDH:DHE+AESGCM:DHE:!RSA!aNULL:!eNULL:!LOW:!RC4'
Manually check certificate revocation status from OCSP responder
This is a multi-step process:
Openssl Generate Aes 256 Key Size
- Retrieve the certificate from a remote server
- Obtain the intermediate CA certificate chain
- Read OCSP endpoint URI from the certificate
- Request a remote OCSP responder for certificate revocation status
Openssl Generate Aes 256 Key
First, retrieve the certificate from a remote server:openssl s_client -connect example.com:443 2>&1 < /dev/null | sed -n '/-----BEGIN/,/-----END/p' > cert.pem
You’d also need to obtain intermediate CA certificate chain. Use -showcerts flag to show full certificate chain, and manually save all intermediate certificates to chain.pem file:openssl s_client -showcerts -host example.com -port 443 </dev/null
Read OCSP endpoint URI from the certificate:openssl x509 -in cert.pem -noout -ocsp_uri
Request a remote OCSP responder for certificate revocation status using the URI from the above step (e.g. http://ocsp.stg-int-x1.letsencrypt.org). openssl ocsp -header 'Host' 'ocsp.stg-int-x1.letsencrypt.org' -issuer chain.pem -VAfile chain.pem -cert cert.pem -text -url http://ocsp.stg-int-x1.letsencrypt.org
Resources
I’ve put together a few resources about OpenSSL that you may find useful.

Openssl Generate Random Aes 256 Key
OpenSSL Essentials: Working with SSL Certificates, Private Keys and CSRs | DigitalOcean — https://www.digitalocean.com/community/tutorials/openssl-essentials-working-with-ssl-certificates-private-keys-and-csrs
Openssl Generate Aes 256 Keys
The Most Common OpenSSL Commands — https://www.sslshopper.com/article-most-common-openssl-commands.html
Openssl Generate Aes 256 Key Base64
OpenSSL: Working with SSL Certificates, Private Keys and CSRs — https://www.dynacont.net/documentation/linux/openssl/